Radio Sentinel
After 2 years of development and thousands of hours of work Armadillo Phone is proud to announce our new “Radio Sentinel” app.
Radio Sentinel helps Armadillo Phone defend against cellular attacks. Cellular attacks are some of the most common mass surveillance and mobile hacking techniques. These attacks intercept or track your phone’s cellular connection. Cellular attacks are widespread and are used by both criminals and governments around the world. Both the latest versions of iOS and Android are vulnerable.
To our knowledge, Armadillo Phone is now the only secure phone in the world capable of detecting cellular attacks. Radio Sentinel requires extensive modifications to Android, so unfortunately it can’t easily be ported to other devices besides Armadillo Phone.
Features
Radio Sentinel is capable of detecting cellular attacks over 2G, 3G, 4G and 5G. These include IMSI catchers, silent SMS and SS7 attacks.
Radio Sentinel works offline, without needing to upload or download data from a third-party server.
Radio Sentinel will trigger a notification when a warning is detected. If that attack is high severity, you will automatically be disconnected from the cellular network. By default, while Radio Sentinel is active only 4G and 5G networks are allowed. This is to prevent “downgrade attacks”, caused when an IMSI catcher forces the victim to use an older or weaker network so it can be attacked.
Screenshots
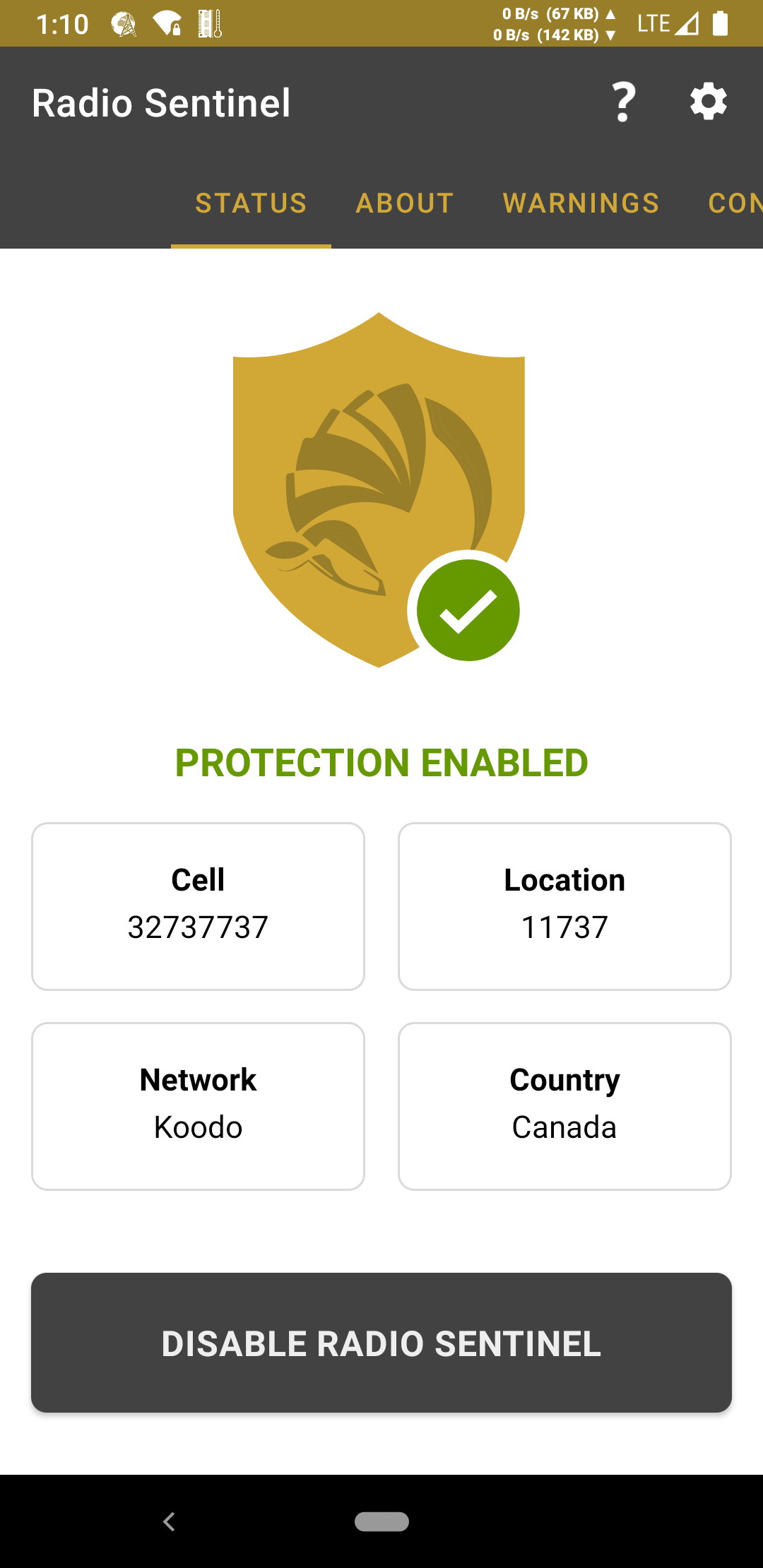
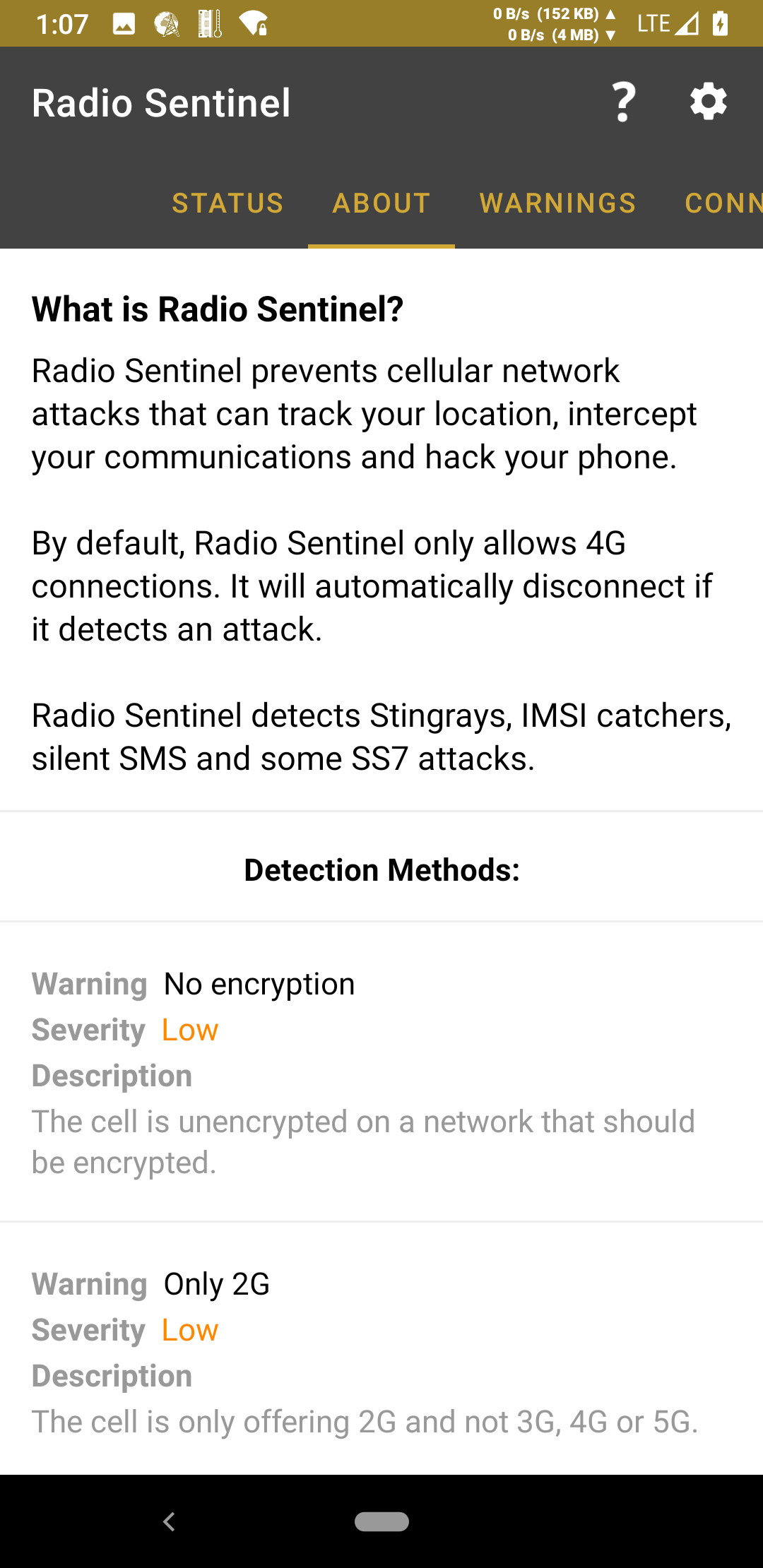
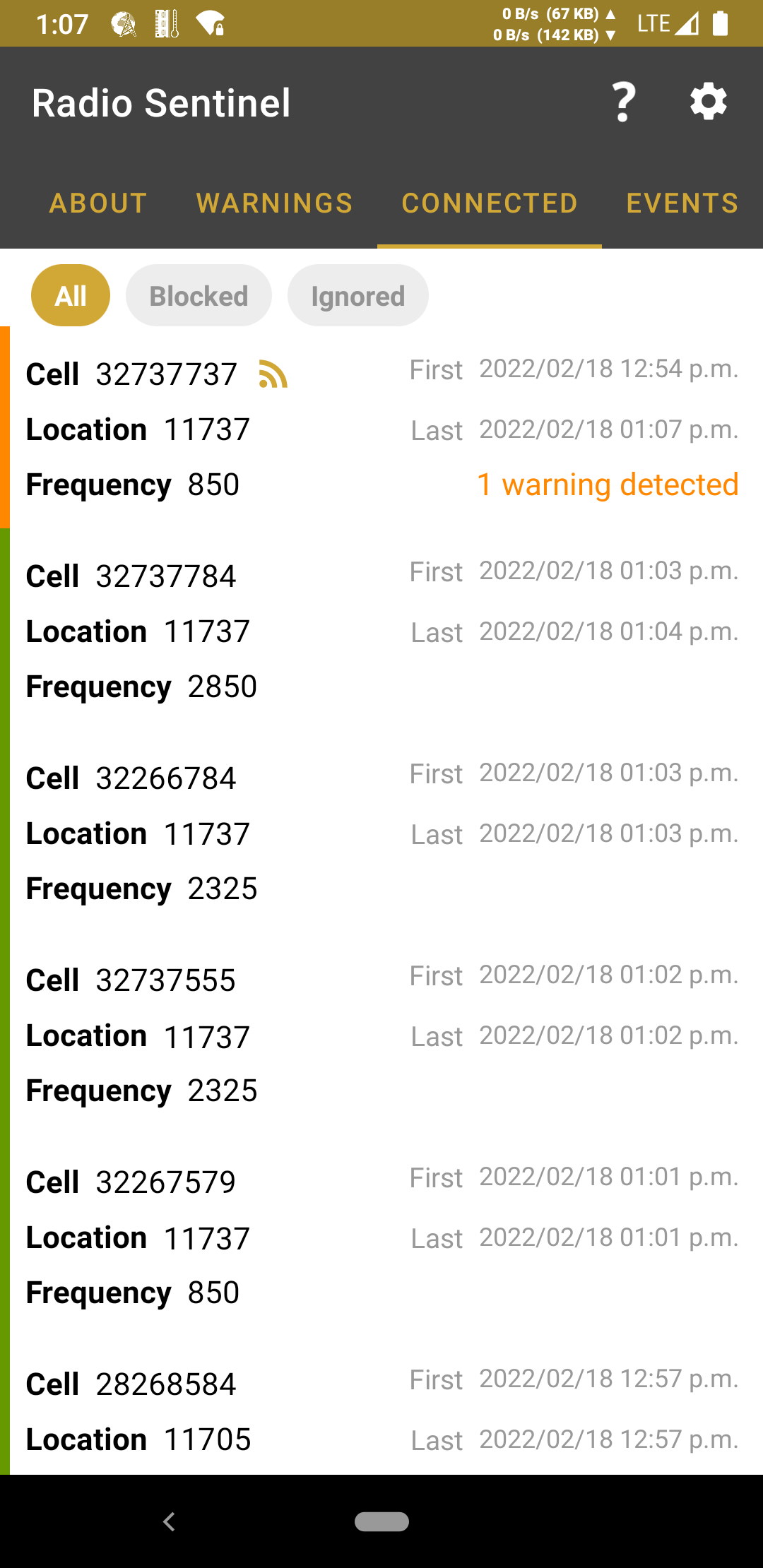
Warnings
The cellular network is very diverse and inconsistent. Some networks don’t use encryption or have misconfigured values that could appear suspicious. Because of this, there are often false positives that look like attacks but aren’t. In order to help combat this noise while still being as transparent to the user as possible, warnings are ranked by likelihood of being a false positive:
- Low severity warnings are often false positives.
- Medium severity warnings are rarely false positives.
- High severity warnings have no known false positives.
Low severity:
- Warning: No encryption
-
Description: The cell is unencrypted on a network that should be encrypted.
- Warning: Only 2G
-
Description: The cell is only offering 2G and not 3G, 4G or 5G.
- Warning: Weak encryption
-
Description: The cell is weakly encrypted ( A5/2 )
- Warning: Encryption downgrade
-
Description: The cell went from being encrypted to unencrypted.
- Warning: No neighbors
-
Description: The cell is not advertising any neighbors.
- Warning: Bad fingerprint
-
Description: The cell is advertising capabilities that doesn't match other cells on the same network.
- Warning: Different location
-
Description: The location ( LAC ) of the cell differs from the location of all neighboring cells.
- Warning: Noisy location
-
Description: The cell's neighbors are reporting a high amount of noise, which may indicate cells are being jammed.
- Warning: New location
-
Description: The cell is using the same cell ID seen previously, but with a different location. This could indicate an attacker moved to a new location.
- Warning: New frequency
-
Description: The cell is using a cell ID that was seen before but on a new frequency. Legitimate cells typically use 1-3 frequencies, attackers may use many frequencies.
- Warning: Invalid cell
-
Description: The cell is using an invalid cell ID. For 2G they must be less than 65535, for 3G and 4G they must be less than 268435455.
- Warning: Incorrect frequency
- Description: The cell is using a frequency the network it's claiming to be from is not allowed to use.
Medium severity:
- Warning: Incorrect country
-
Description: The cell is operating in the wrong country for the network it's claiming to be from.
- Warning: Unknown network
-
Description: The cell is using an unknown mobile network code.
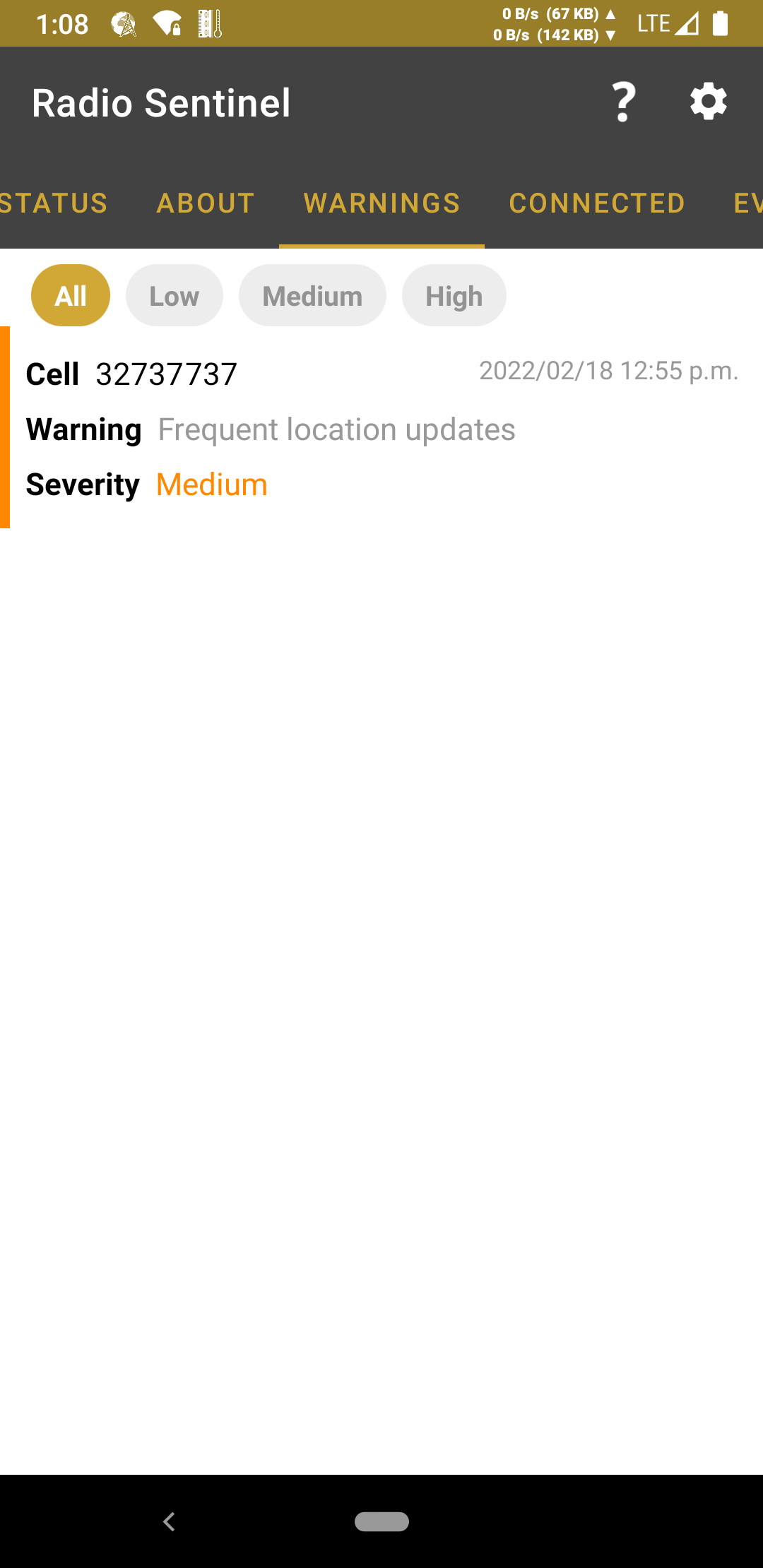
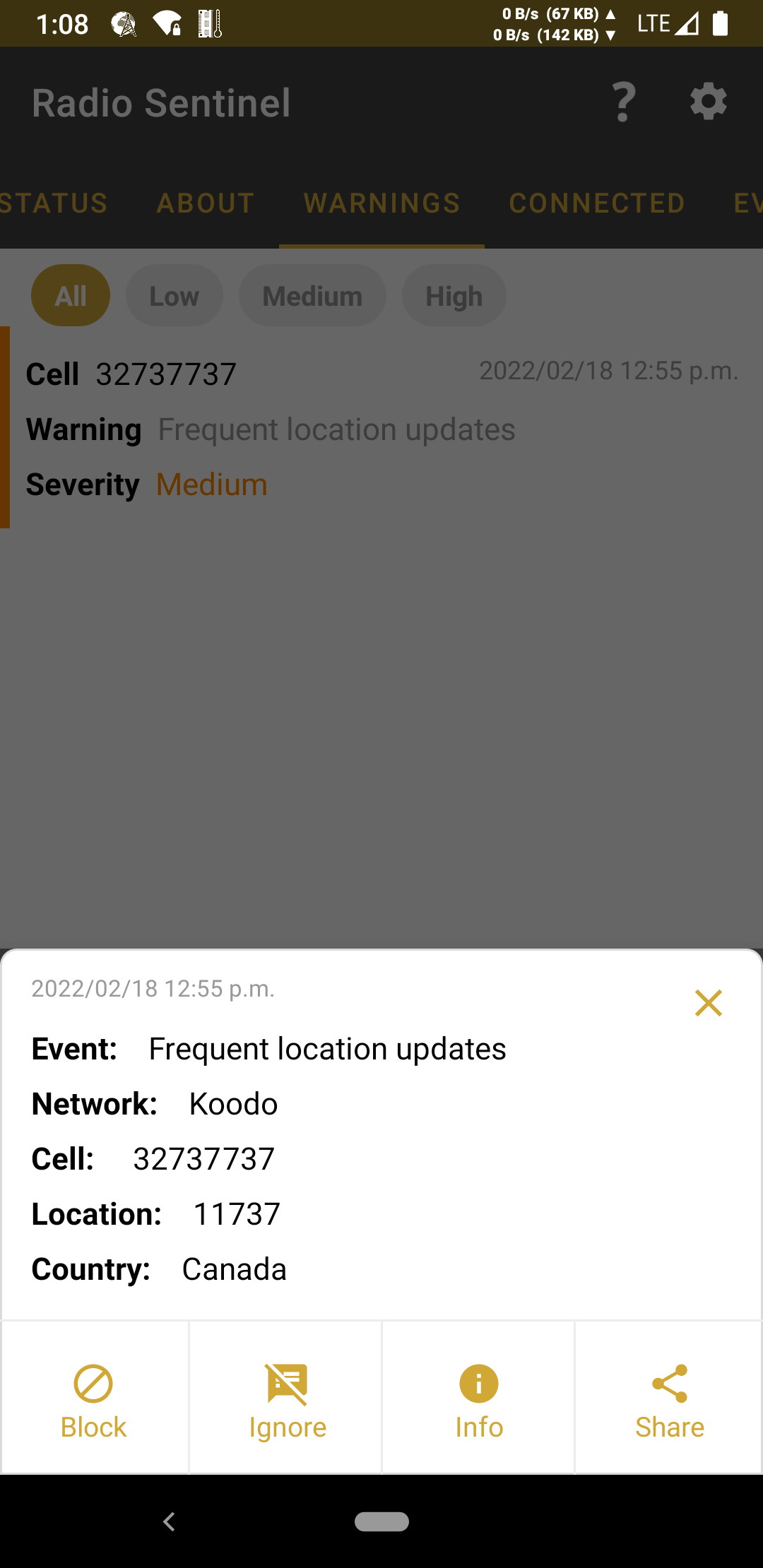
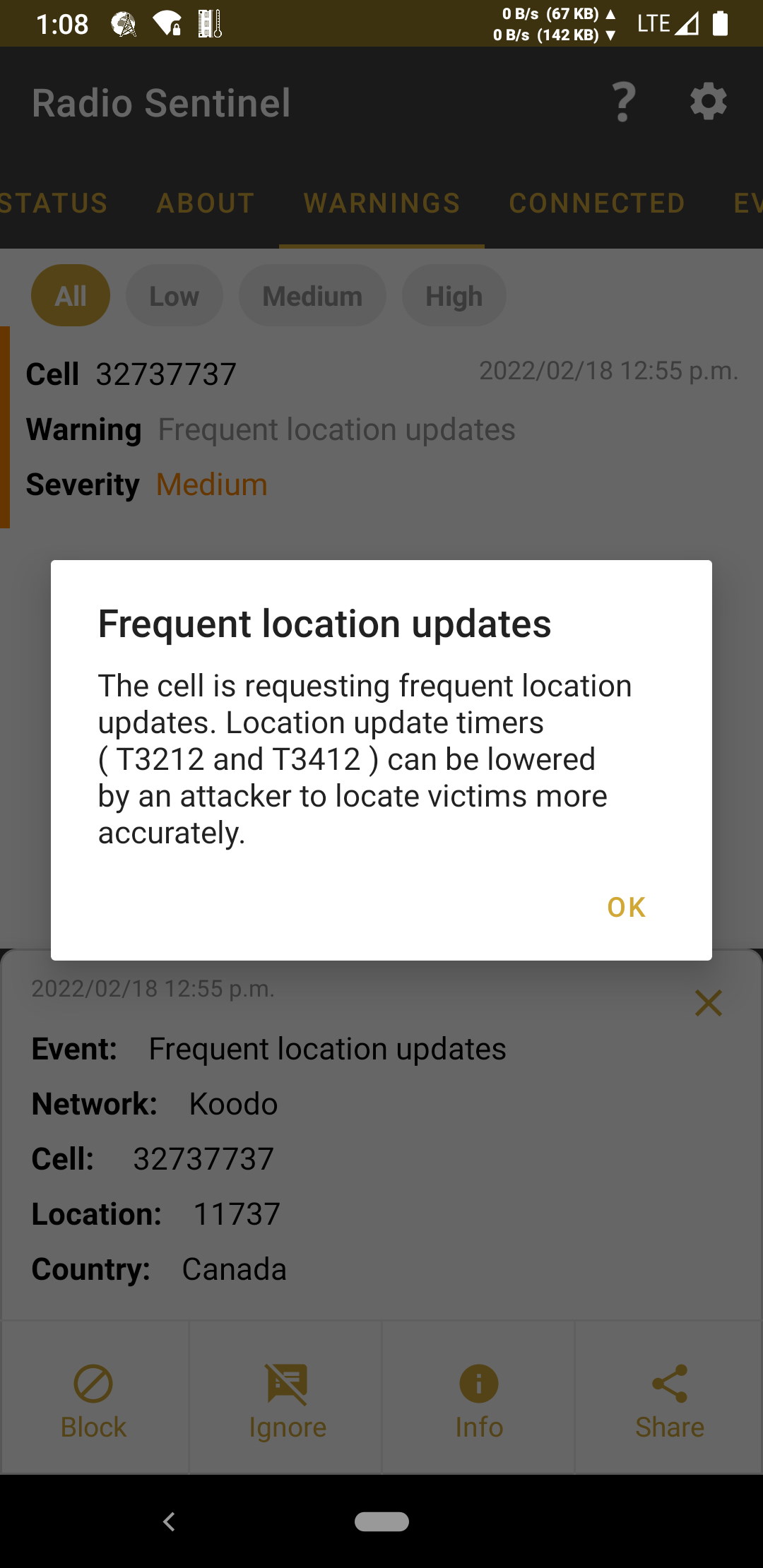
- Warning: Frequent location updates
-
Description: The cell is requesting frequent location updates. Location update timers ( T3212 and T3412 ) can be lowered by an attacker to locate victims more accurately.
- Warning: TAU reject
-
Description: A suspicious Tracking Area Update reject message was received, which can be used to get your phone's ID ( IMEI ) and track your location.
- Warning: Binary SMS
- Description: A binary SMS was received, which can be used to track your location.
High severity:
- Warning: Silent SMS
-
Description: A silent SMS was received, which can be used to track your location.
- Warning: Empty paging request
-
Description: A paging request without a call or SMS was received. Empty paging requests can be used in SS7 attacks to track your location.
- Warning: Fake strength
- Description: The cell is using a very high cell reselect offset. Attackers use fake reselect offsets to force victims to connect.
Testing
Radio Sentinel was tested extensively in Vancouver during development. It has been tested by early adopters against real attack equipment successfully. Now that it’s been released, we are continuing to improve it using the bug reports customers send us. We’re in the process of arranging a formal third-party audit to test Radio Sentinel against more attack equipment. If you have an IMSI catcher and would like to attack an Armadillo Phone, please contact us.
The most secure phone
To learn more about Armadillo Phone, please click here.
If you want to purchase an Armadillo Phone, please visit our store.
-
Published on: Mar 25th, 2022
