Armadillo Phone is designed to maximize privacy and security. If you're forced to unlock it, you can instead reveal a fake decoy user. It can detect Wi-Fi, cellular and forensic attacks. The operating system prevents vulnerabilities that can be used by hackers. If an Armadillo Phone is compromised you have many methods to erase it. Cameras or microphones can be removed. Hardware accessories further enhance your security.
Armadillo Phone is decentralized. Use a public server or host your own private server. Multiplexing hides your metadata, to bypass surveillance and firewalls. All connections use pinned certificates, for maximum security. The server isn't trusted and can't access your sensitive data. End-to-end encryption protects your communications. LEARN MORE
Cameras or microphones can be removed. Devices are inspected prior to shipping. Shipments use tamper-evident packaging.
Armadillo Phone comes with accessories to help prevent wireless attacks, physical attacks and theft. Use an Armadillo SIM card, your existing SIM card or Wi-Fi only.
Armadillo Phone uses a hardened fork of Graphene OS. The kernel, system and apps have been modified to improve security. File encryption has been hardened to encrypt each user separately and resist bruteforcing. Unsafe features have been removed. LEARN MORE
If you're forced to unlock your Armadillo Phone you can login as a fake user. Switch to other users by entering their password at the lockscreen. LEARN MORE
Enter a "wipe password" to erase your Armadillo Phone, erase other Armadillo Phones remotely, or have your Armadillo Phone erase itself if it's not unlocked after a certain time. "Incognito mode" creates a user that's erased when you logout.
Detect and prevent attacks:
![]() Radio Sentinel: Detect cellular attacks
Radio Sentinel: Detect cellular attacks
![]() Wi-Fi Sentinel: Detect Wi-Fi attacks
Wi-Fi Sentinel: Detect Wi-Fi attacks
![]() RAM Sentinel: Prevent forensic attacks
RAM Sentinel: Prevent forensic attacks
![]() Theft Sentinel: Prevent theft
Theft Sentinel: Prevent theft
Radio Sentinel mitigates cellular network attacks that can track your location, intercept your communications and hack your phone. Radio Sentinel only allows 4G connections by default. Radio Sentinel detects IMSI catchers, silent SMS and some SS7 attacks. It will automatically disconnect if it detects an attack. LEARN MORE
Wi-Fi Sentinel mitigates Wi-Fi network attacks. Wi-Fi Sentinel detects KARMA and ARP poisoning attacks. It will automatically disconnect if it detects an attack.
Theft Sentinel pairs with your Armadillo Beacon over Bluetooth to prevent theft. If your Armadillo Phone and Armadillo Beacon become separated they will both trigger an alarm. Unless they're reconnected or your phone is unlocked, your Armadillo Phone will eventually shut down.
RAM Sentinel monitors your Armadillo's temperature and prevents cold-boot attacks designed to extract the password from your device using cold temperatures. It will shutdown your Armadillo Phone if it detects an attack.
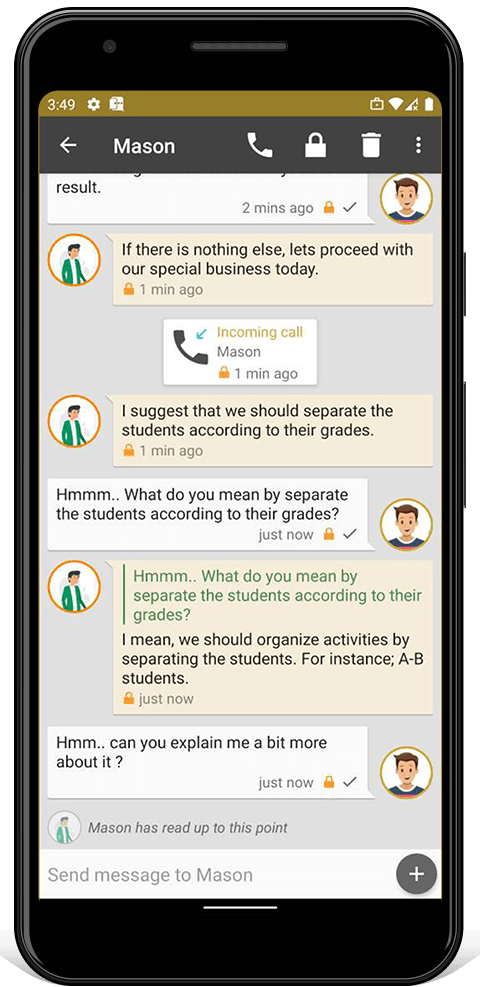
Armadillo Chat is a secure instant messaging app. It uses OMEMO end-to-end encryption, so your messages are safe even if the server is compromised. You can use multiple methods to verify your friend's encryption identities. Armadillo Chat automatically warns you about potential impostors in your contacts list and other devices logged into your account. Set automatic self-destruction timers, remotely erase messages or whole conversations. LEARN MORE
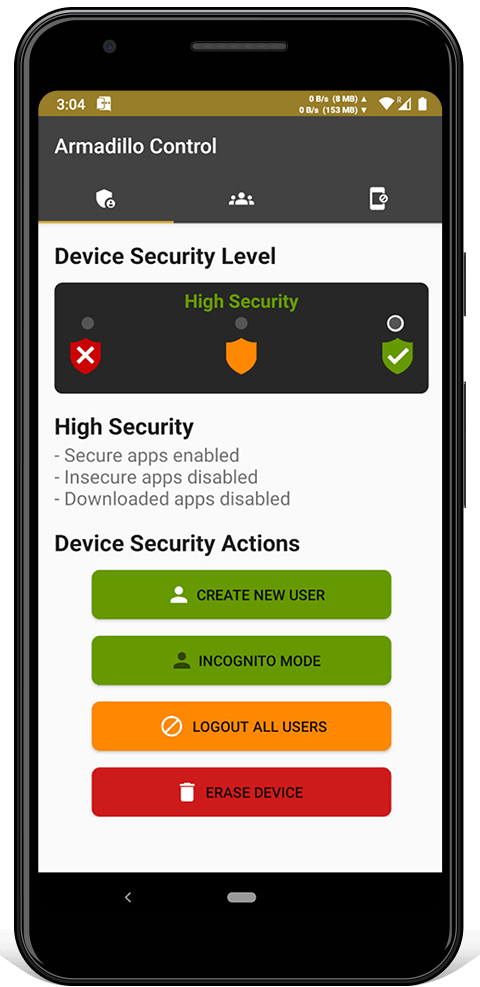
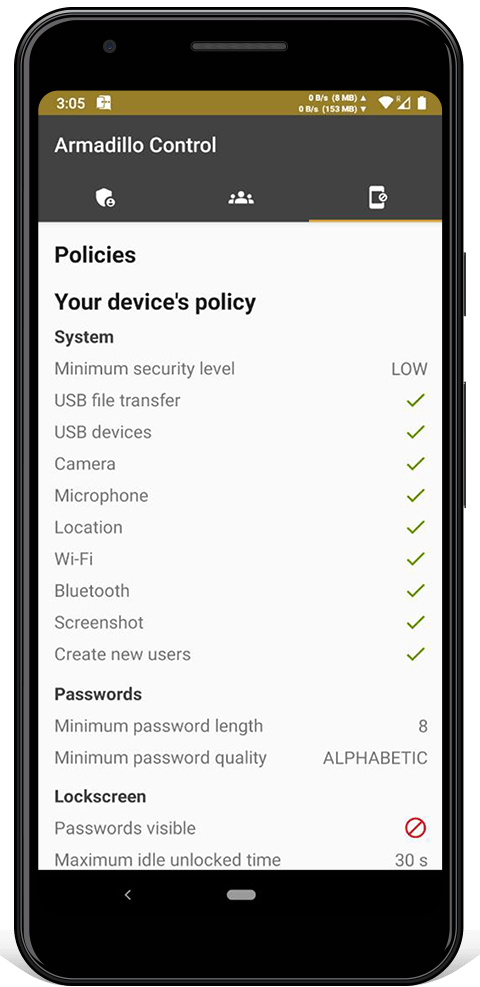
Armadillo Control is used to remotely manage other Armadillo Phones. You can shutdown, alarm, erase and change the settings. It sends end-to-end encrypted commands using Armadillo Chat, so if a server is compromised it can't send malicious commands.
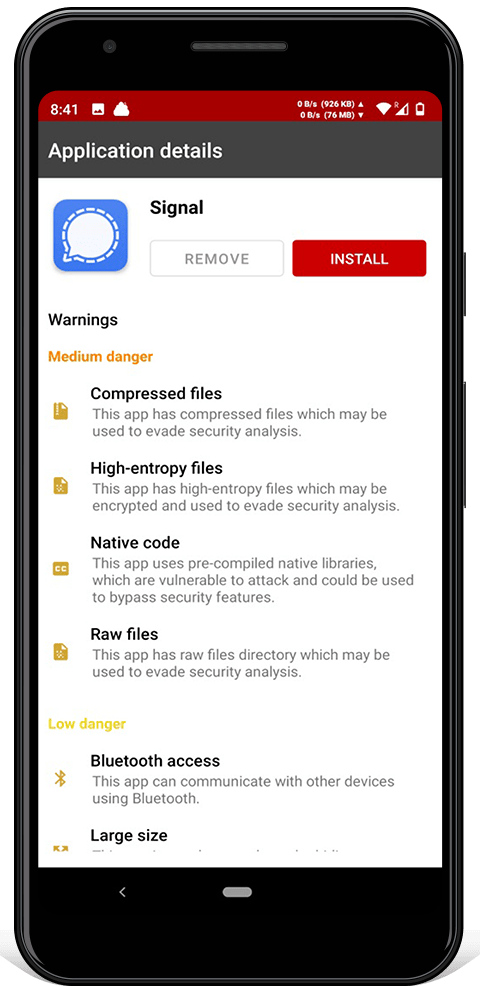
Install allows you to install new apps. After being downloaded, an app is scanned using heuristic analysis. Warnings are shown prior to installation being allowed. To prevent installing fake apps, the keys for popular apps are embedded. Updates to apps must be done with the existing key, so a server can't send a malicious update.

The "network indicator" appears next to the Wi-Fi and cellular icons. It shows how much data is being transferred, to detect suspicious network activity.
All Armadillo software use the same colors: red is insecure, orange is dangerous and green is secure.
Easily change between three 'security modes' depending on what you're doing: low security, medium security or high security.
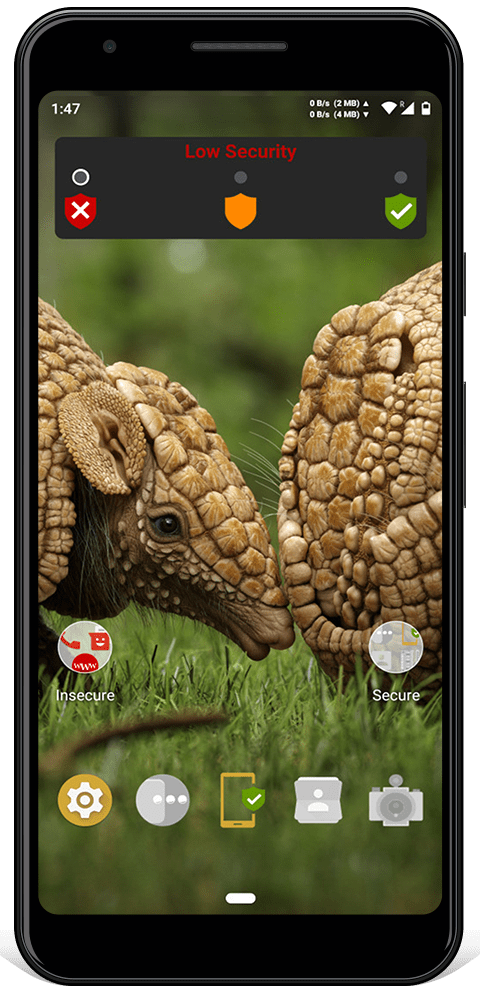
 Low Security
Low Security 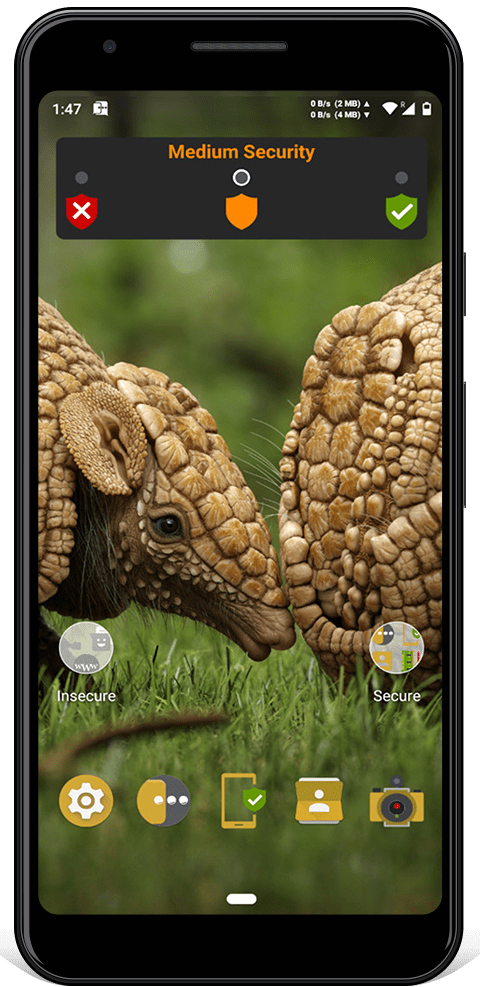
 Medium Security
Medium Security 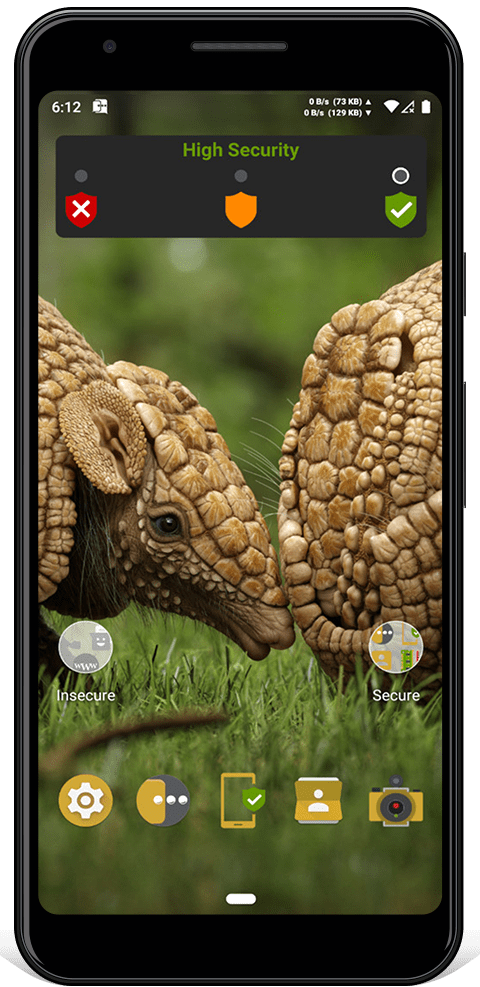
 High Security
High Security Security patches from newer versions of the Linux kernel have been backported to Armadillo Phone. These include FORTIFY-SOURCE-STRING-STRING, HARDEN-BRANCH-PREDICTOR, INIT-ON-FREE-DEFAULT-ON, INIT-ON-ALLOC-DEFAULT-ON, INIT-STACK-ALL, BUG-ON-DATA-CORRUPTION and many more. Entropy for kernel userspace ASLR has been increased to mitigate memory corruption exploits.
Android's build process has been strengthened, including improvements for stack probes, bounds checking, frame pointers and automatic variable initialization. The compiler toolchain and libc have been hardened. The malloc implementation has been replaced with hardened_malloc, which is further tuned to enhance security and increase quarantine space. Cross-user interactions have been blocked at the framework level, to prevent leaks.
Historically, the Android media stack has been very vulnerable, so Armadillo has hardened it to resist attacks. The oldest, least used and riskiest codecs ( such as H263 and software codecs ) have been removed. Scudo has been expanded in scope and hardened. The mediadrmserver and drmserver have been removed. MMS auto-retrieval is permanently disabled to mitigate remote attacks.
TLS multiplexing prevents leaking protocol metadata and bypasses firewalls. Network time is synchronized using TLS, instead of NTP. Name resolution is done using DoT ( DNS over TLS ), instead of plaintext DNS. TLS session tickets are disabled to prevent tracking across connections. The browser is only enabled in low security mode. You can disable networks like Wi-Fi, cellular or Bluetooth using MDM security policies.
Share your VPN connection with devices connected to your Armadillo Phone's hotspot, turning your Armadillo Phone into a hardware VPN.
Armadillo OS has improved Graphene's storage encryption by encrypting the metadata of each user separately. So even if your Armadillo's hardware security is compromised, revealing a user's password won't affect the security of other users metadata.
On first boot, a random amount of "fake users" are generated with a random amount of data, to help prevent attackers from detecting real users.
Scrypt KDF work factors have been strengthened ( from 15:3:1 to 19:4:1 ) to resist bruteforcing. LEARN MORE
Unsafe software components have been removed to prevent vulnerabilities. This includes tracking software used by Google and third-parties. Dangerous permissions (like internet or location access) given to the Camera and Contacts apps have been removed. Safe default settings have been set, such as requiring strong passwords, hiding notification content and disabling biometrics. If your Armadillo Phone is remotely wiped, it won't indicate it's erasing your data. Enabling developer options has been disabled. The ability to toggle Wi-Fi, Bluetooth or airplane mode from a locked phone has been disabled.
Armadillo Phone uses multiple layers of redundant encryption to protect your data. TLS certificates are pinned to prevent MitM attacks. TLS session tickets are disabled to prevent tracking across connections. TLS multiplexing prevents leaking protocol metadata and bypasses firewalls.
Protocol: Deniable multi-user FBE
Purpose: Protect the data stored on an Armadillo Phone.
Content encryption: AES-256-XTS
Metadata encryption: AES-256-XTS
KDF: Scrypt 19:4:1
Protocol: Android Verified Boot 2.0
Purpose: Protect the integrity of the operating system.
Key: RSA-2048
Checksum: SHA-256
Protocol: SQLCipher
Purpose: Protect the notes used by the Notepad app.
Content encryption: AES-256-CBC
KDF: Scrypt 13:8:1
HMAC: SHA-512
Protocol: 4G LTE
Purpose: Protect the connection between an Armadillo SIM and the cell tower.
Key: SNOW-128
Content encryption: SNOW
Protocol: OpenVPN
Purpose: Protect the connection between the cell network and an Armadillo Server.
Handshake: ECDHE
Key: RSA-4096
Content encryption: AES-128-CBC
HMAC: SHA-256
Protocol: Pinned TLS 1.3
Purpose: Protect the connection between an Armadillo Phone and Armadillo Server.
Handshake: ECDHE
Key: RSA-4096
Content encryption: AES-256-GCM
HMAC: SHA-512
Protocol: OMEMO
Purpose: Protect the messages between Armadillo Phones.
Handshake: X3DH ( Curve25519 )
Authentication: ECC-256
Key: ECC-256
Content encryption: AES-256-CBC
HMAC: SHA-256
Protocol: Zero-knowledge password proof
Purpose: Authenticate your Armadillo Phone to an Armadillo Server.
Token: JWT
KDF: Scrypt 15:10:1
Digest: SHA-256
Instead of trusting us to host your accounts, you can run your own Armadillo Server. Your Armadillo Server can host secure communications, new apps to download and encrypted internet infrastructure ( DNS and NTP ). You can run Armadillo Phones on your own offline network.
Armadillo Phones connect all protocols ( HTTP, XMPP, DNS, etc. ) to the Armadillo Server on the same port, with the same domain, and encrypt all connections identically. To an attacker intercepting the connection, everything looks like encrypted HTTPS traffic. This prevents leaking protocol metadata, which could be used to identify users with timing attacks. It also allows connections to bypass some firewalls and mitigates passive metadata surveillance.